Vulnerability analysis and defense framework for the cybersecurity of a traffic control system
Traffic signals are among the most popular targets of hacking in fiction. In a number of movies, TV shows and video games, traffic signals are manipulated to let the hacker and his/her friends make their escape from police pursuit. These scenes may not be realistic now because existing transportation infrastructure is mostly deployed in a private wired network, and control decisions are made based on infrastructure-based sensors (e.g., in-pavement loop detectors). The only way that hackers can compromise the system is through the central traffic management systems such as traffic management centers (TMCs), which are usually firewall protected.
With the development of connected and automated vehicle (CAV) technology, vehicles and infrastructure will be connected through wireless communications (e.g., Dedicated Short-Range Communication [DSRC] or the cellular network), which might open a new door for cyber attackers. Cybersecurity of transportation systems has been a growing research area in the past decade, but most efforts are focused on inter-vehicle communications. As a critical part of the transportation infrastructure, existing traffic control systems have a profound impact on the safety and efficiency of urban traffic flow, but are highly vulnerable to cyberattacks because of a systemic lack of security consciousness. It is not clear what types of cyberattacks can be performed through infrastructure-to-infrastructure (I2I) and vehicle-to-infrastructure (V2I) communications, whether such attacks can create critical failure to traffic control systems, what the impacts of cyberattacks on traffic operations are, and what remedies exist to detect the attacks and protect the system.
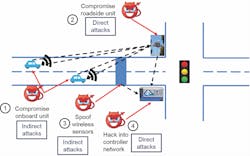
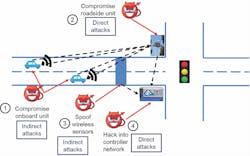
Figure 1: Four possible attack surfaces include signal controllers, vehicle detectors, onboard units and roadside units.
Threat model
Researchers from the Transportation Research Institute and the Department of Electrical Engineering and Computer Science at the University of Michigan have conducted a systematic study of the vulnerabilities of the existing traffic control system in a connected environment and identified four possible attack surfaces, including signal controllers, vehicle detectors, onboard units (OBUs) and roadside units (RSUs), as shown in Figure 1. Based on these attack surfaces, two types of attacks have been identified: direct attack and indirect attack. Direct attack refers to hacking into the signal controller and RSU and changing the signal-timing plans directly. To launch direct attacks, an attacker needs physical access to the devices, which requires the attacker to open the signal controller cabinet and connect to the signal controller or the RSU using an Ethernet cable. Indirect attack refers to tampering with data from vehicle detectors and/or OBUs. Usually, indirect attacks are more realistic to conduct. One recent example is when an Argentinian security expert hacked into New York City’s wireless vehicle detection system with a cheap wireless device. The vulnerabilities he found allowed anyone to take complete control of the devices and send fake data to the traffic control systems. Although traffic signals were not directly controlled, fake vehicle data could cause severe traffic congestion and increase crash risks.
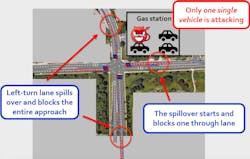
Figure 2: Results of the simulated attack.
Attack model
An attack model was designed focusing on indirect attacks. It is assumed that falsified traffic data is sent through the compromised devices to the traffic control system. The attacker may have different goals, including increasing system chaos (e.g., generating traffic congestion), gaining personal benefits (e.g., escape from a police pursuit), and causing safety issues (e.g., creating more conflicts). Moreover, the attacker has a budget limit, which means that the number of vehicle detectors and OBUs that can be compromised is limited. As a result, the attacker needs to find and attack critical locations in the traffic network to maximize the damage.
A simulation model of a real-world intersection was built in VISSIM, a microscopic traffic simulator, to evaluate the impact of the spoof attacks. It is assumed that the attacker compromised his/her own vehicle to send falsified vehicle trajectories in terms of location and speed. The attacker wants to increase system chaos by maximizing the total number of vehicles at the intersection. The attacker’s vehicle sits at the gas station near the intersection, where it also can receive vehicle trajectory data (e.g., basic safety messages) from other vehicles. By analyzing the signal control logic and other vehicles’ status, the attack vehicle can pretend to be anywhere on the roadway at any speed. The wrong information is transmitted to the control system to mislead the controller to make less optimal solutions. Figure 2 shows the attack results. Because the attack vehicle makes the control system inaccurately estimate traffic conditions and allocate green time inefficiently, congestion starts to build up at the intersection cycle by cycle. Especially for left-turn phases at northbound, southbound and westbound directions, left-turn vehicles spill back to the through movement lane, which blocks through vehicles and further reduces the intersection capacity.
Furthermore, the attack model was tested at a real-world corridor, which consisted of six consecutive intersections. Traffic data was collected during evening peak driving time to calibrate the simulation model and serve as the baseline. Again, only one location (signal phase) was attacked. Figure 3 shows the vehicle delay under the most effective attack scenario: Intersection 2 westbound through movement. In the network, red and orange colors mean congestion, while green and white colors mean freeflowing traffic conditions. Because of the attack, the westbound direction of intersections 2, 3, 4 and 5 are in oversaturated condition. The vehicle queue starts to accumulate at intersection 2 and eventually propagates to intersections 3, 4, and 5. Not only the main corridor, but the side street of intersection 5 (northbound direction) also becomes very congested. It is caused by the spillover on the main corridor, which prevents vehicles turning left from the side street. Quantitative results show that by attacking only one critical location, the vehicle delay of the entire network is increased by about 200%. This result also can help practitioners to identify critical intersection approaches on the roadway, which is helpful in designing a more resilient transportation network.
Figure 3. Vehicle delay under most effective attack scenario: Intersection 2 westbound through movement.
Defense model
To overcome cybersecurity vulnerabilities and protect the traffic control system, a trajectory based hierarchical defense (TBHD) framework is developed. This defense framework adds an additional layer of data filtering before directly applying to the control system. TBHD consists of three hierarchies. Level 1 is a pointwise checking that determines if elements in the received trajectory data fall within feasible ranges. For example, the location of the trajectory data must fall within the road of interest (RoI) with a stretched boundary tolerance. The speed of the trajectory data must be between zero and free-flow speed. The acceleration should fall into the range between minimum acceleration and maximum acceleration. Finally, the heading of a vehicle must be in the direction of its traveling approach.
Level 2 is a multiple-point checking that determines if the consecutive trajectory points obey the laws of physics. For instance, using the location information of a trajectory point at two different time points, the speed of the vehicle can be estimated based on the definitional equations. The absolute difference between the estimated speed and the measured speed should be less than a threshold. The acceleration of a vehicle can be checked in a similar manner. Assuming a constant acceleration within a short time period, the location, speed and acceleration information of a vehicle at a previous time step can be input into the equations of motion to predict the location of the vehicle at the next time step. The absolute difference between the predicted and measured location should be smaller than a threshold.
Level 3 is a multiple-trajectory checking that determines if two vehicles’ trajectories overlap with each other. All trajectories can be classified into four bins: real-vehicle, unclassified, suspicious-fake-vehicle and identified-fake-vehicle. A complex logic is designed to categorize overlapping trajectories into different bins. To keep sufficient vehicle data while avoiding potential cyberattacks, trajectory data from the unclassified and real-vehicle bins will be passed to the traffic control system, and data from both the suspicious-fake-vehicle and identified-fake-vehicle bins will be blocked.
Generally speaking, the system impact of a data spoofing attack is positively correlated with the size of a high-dimensional space, which represents all possible trajectories. Because the TBHD framework can reduce the size of the high dimensional trajectory space level by level, it can greatly reduce the potential system impact caused by trajectory spoofing attacks. Attack results showed that even with one compromised vehicle or detector, a data spoof attack can cause significant damage to the transportation system. Comprehensive simulation studies have revealed that the proposed TBHD framework is able to detect most of the data spoofing attacks in less than one second. The defense model can effectively reduce the feasible trajectory space level by level, thus filtering most trajectory spoofing attacks.